If we talk about finding out someone location using his phone, you would probably think about some scene you saw in a movie where the police would try to find a hostage-taker while he’s calling to ask for a ransom. But did you know that this is not the only usage of cellular tower location? In fact, walking down the street with your phone turned on will produce some level of localisation logs. This could even be used by authorities as they did in Taiwan to track down people not respecting the mandatory quarantine during the Covid crisis (see this article). If you’re thinking that you are not impacted, think again. Some similar tracking is also of actuality in Western countries.
In today’s article, we will introduce how the cellular network works, what kind of data is collected, and how this data can be used to locate you.
Mobile Communication Technologies and Radio Waves#
The mobile network is using radio signals to allow its various components (cell towers and mobile devices) to communicate together. In this part, we will quickly go through the various technologies used, and some of the techniques that allow multiple devices to communicate together without causing interferences.
Network Standards#
There are various phone networks standard generations. In fact, if you own a phone, you have heard about them: this is the “4G” that you have most of the time next to your signal bars.
1st Generation Networks (1G)#
1G was created in 1984. It was an analogue system only allowing voice transfer. It is now deprecated and not in use anymore.
2nd Generation Networks (2G)#
2G was introduced in 1991. It is now deprecated as well, but this is still in use today. 2G introduces digitally encoded signals (compared to analogue ones before,) and the possibility to send texts and use the Internet. Some of the standards it uses are:
- GSM (Global System for Mobile) was the first 2G system. It wasn’t allowing access to the Internet, but it was possible to use SMS messages
- GRPS (General Packet Radio Service) is an improvement of GPS. It allows connecting to the internet and sending/receiving MMS messages. It is sometimes referred to as 2.5G.
- EDGE (Enhanced Data Rates for GSM Evolution) was introduced in 2003, and is the final 2G evolution and is considered as pre-3G. It is an improvement of the previous standard and allows data transmission up to 473 kbps.
The technologies used by 2G to manage the radio channel access are the following (we will talk more about them later):
- TDMA (Time Division Multiple Access)
- FDMA (Frequency Division Multiple Access)
- CDMA (Code-Division Multiple Access - only with EDGE)
3rd Generation Networks (3G)#
3G was introduced in 2000 and allows faster data transfers than its predecessors. It uses W-CDMA (Wideband CDMA) and allows up to 2 Mbps data rate when stationary and 144 kbps when driving in a car.
As for 2G, 3G had multiple enhancements aiming to improve its performances
- HSDPA (High-Speed Downlink Packet Access), also known as 3.5G allows up to 14 Mbps downstream and 2 Mbps upstream
- HSUPA (High-Speed Uplink Packet Access), also known as 2.75G boosts upstream rate up to 2.8 Mbps
- HSPA+ (Evolved High-Speed Packet Access) supports up to 168 Mbps downstream and 22 Mbps upstream
LTE - pre-4G but Marketed as 4G#
LTE (3G Partnership Project - Long Term Evolution) is a pre-4G system that offers increased performances compared to 3G but still doesn’t reach the full 4G potential. It can offer up to 300 Mbps downstream and 75 Mbps upstream and improves data transmission while in movement by replacing CDMA with OFDMA (Orthogonal Frequence-Division Multiple Access).
LTE doesn’t support voice calls, so 2G, 3G, or voLTE are used when necessary.
Networks Frequencies#
We mentioned that in cellular networks, the data is exchanged through radio waves. Depending on the technology used, the available frequencies are different. For example, 3G can operate using the 800, 850, 900, 1,700, 1,900, and 2,100 MHz bands while GSM only supports 850, 900, 1,800, and 1,900 MHZ bands. Depending on the country, it is also possible that not all of the available bands are used.
Usually, higher frequencies will transfer data faster but within a shorter range, while lower frequencies will carry data to longer distances but more slowly.
Channel Access Methods#
We previously mentioned FDMA, TDMA, CDMA, and OFDMA. Now that we also talked about the frequencies, we can go into more details regarding what they do.
These three acronyms are channel access methods used by radio technologies. Imagine that you have multiple endpoints sending data using the same radio frequency; if nothing is done, the data will just collide and a device listening to this radio channel would not understand anything. The channel access methods aim to solve this problem.
FDMA#
The Frequency Division Multiple Access will divide the available bandwidth into multiple non-overlapping channels that it will assign to the connected devices. For example, if we have a tower using a bandwidth B and two connected devices, device 1 will be assigned the first 200 KHz, the next 50 MHz will be unassigned to avoid overlap, and device 2 will be assigned the next 200 MHz. This way, all devices can communicate at the same time and the tower can tell their traffic apart.
TDMA#
The Time Division Multiple Access requires more synchronization between the devices. All the devices using a tower will be able to use the whole bandwidth, but they will have a specific timeslot during which they are allowed to communicate, so it is important that their clocks are strictly the same.
CDMA#
With the Channel Division Multiple Access techniques, all of the devices can transmit data at the same time using the same frequency. Each device is using a specific code sequence when transmitting data, which allows telling the different signals apart. The main difference between CDMA and W-CDMA is that the latter supports a wider bandwidth.
The Phone Network#
The phone network requires multiple components to be operational. Your phone will only directly interact with the cell towers to send and receive data, but these towers will use different systems to properly authenticate the devices, and route the relevant calls/data to the right place.
Base Transceiver Stations#
Base Transceiver Stations (BST) are the most visible part of the network; they are the cell towers that will send or receive radio signals. Note that they may be referred to as “node B” in 3G networks, “evolved node B” in LTE, or generally as “Base Station.”
Base Stations are usually installed at fixed locations, but it is also possible to install portable ones. This would typically occur when operators expect a larger condensation of people than usual in a certain zone, for example during a concert, and allows the network to not be saturated.
The Base Stations can have two types of antennas:
- Omnidirectional ones are used in low traffic volume areas or for small indoor relays and will receive/broadcast signals within 360 degrees.
- Sector antennas, which are directional. They can have up to 6 sectors but will most commonly use 3, which means that they will broadcast/receive signals in three 120 degree zones.
The following schema shows how the cellular base stations are organized to create a network. We can observe that all of them have a 3-sectors antenna and are placed in a way such as signal can be reached everywhere on the map.
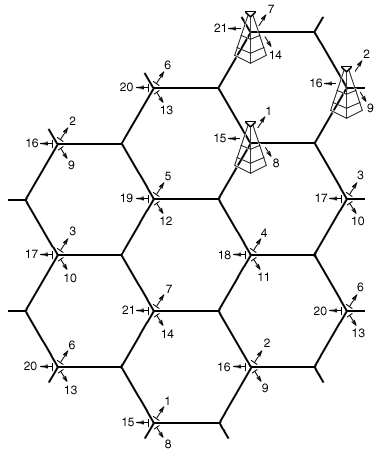
If we look at the top-right cell, we can see that it is surrounded by three base stations, which are broadcasting on frequencies 14, 16, and 1. If you were with your phone in the middle of this cell, you would be able to get signals from the three stations.
The network is made so that:
- Phone network provider companies are using different radio frequencies so that their towers are not interfering with each other (frequencies are usually attributed to companies by state-managed organizations)
- Phone operators are configuring their network in a way that adjacent towers are using different radio frequencies so that they are not interfering with each other
Base Station Controller (BSC)#
The base station controllers can be in charge of controlling one or (more often) multiple base transceiver stations (each BTS has a single BSC). Some of the things they will specifically take care of are:
- The radio frequencies management
- The BTS handovers (i.e.: a device is connected to a BTS, the signal becomes weak, it starts using another BTS with a better signal)
- Setting-up calls
Mobile Switching Center (MSC)#
Mobile Switching Centers are connected to one or multiple BSCs (each BSC has a single MSC) and will interact with various systems in the network to make sure that the various communications are properly routed. Some of their tasks are:
- Connecting to the Home Location Register (HLR) and Visitor Location Register (VLR) to make sure that the devices connected to the base stations are authorized to connect, and to log their calls/text/data usage so that customers can get charged
- Routing calls, SMS, Internet
- Interfacing with the Public Switched Telephone Network (PSTN)
Home Location Register (HLR)#
The Home Location Register is a database that contains data related to mobile subscribers. It is in charge of knowing if a user is allowed to access the network and which services it is allowed to us, knowing how to route transmissions to and from the devices, and how to charge customers. It will also store the last known location for users, and update it when necessary.
To authenticate users, the HLR will store International Mobile Subscriber Identifiers (IMSI) which are stored into Subscriber Identify Modules (SIM cards.)
Visitor Location Register (VRL)#
The Visiting Location Register (VRL) is a database similar to the HLR. It can be used by one or multiple MSCs (each MSC is connected to a single VRL) and will temporarily store data related to the customers connected to its MSCs. It will also store data related to roaming users.
Phones Connection and Antenna Selection#
To summarize some of the elements we discussed until there, let’s go through what happens when you are walking with your phone outside.
- Your phone will scan your surroundings to try and find cell towers
- It will connect with the cell tower that has the strongest signal (unless the tower reached the max number of connections)
- When it connects to the BTS, the MSC will check that the user is allowed to connect using the HLR and VRL, and update various records such as the phone’s location (which BTS it is using)
- Once connected, there will be a full-duplex (FDX) connection between the phone and the BTS
- While you are moving, the phone is still checking which towers are around and which signal is the strongest. If necessary, a handoff can happen (i.e.: the phone will use a different BTS with a better signal). It can be a hard handover (the connection is cut then re-created), or a soft one (the process is transparent and the phone is connected to the network at any time)
- If someone tries to call you, his phone will interrogate the HLR (through the BSC/MSC) to know which BTS you are using, and the call will be routed to you thanks to this information
Tracking Methods#
Now that we finished introducing how the mobile network is working, it is time to see how it is possible to take advantage of the various infrastructures to track networks’ users.
Historical Location#
We mentioned before that when you try to use the network, its components will check if you are permitted to do so. The same components will also log some information about your usage of the network. Some of this information can be stored for a couple of years or less, depending on your provider’s policies (up to 7 for AT&T in the US). In this part, we will discuss what kind of information is stored, and what can be done with it.
Call Details Record#
Every time a mobile device is making a call, information is recorded in the Call Details Records (CDR), mostly for billing purposes (note that similar information will also be recorded for data and SMS activity).
These records will include the following items, with possibly some small variations depending on the network operator:
- The calling and called number
- The start and end date-time
- The identifiers of the first and last towers used when calling (and the sector used)
- The IMSI and IMEI of the phone used
These records will be kept for more or less long depending on the network operator (AT&T stores them for 7 years while Verizon does for 1 year only).
Since we only know which towers took the call, and in which sector, it is not possible to use this data to get a more or less wide-area location. Particularly as the concentration of cell towers depend on the environment (there are a lot of cell towers if you’re in Manhattan, not so much if you’re in the middle of the death valley). A tower could very well cover a 10km radius or a 100m one.
Tower Dump#
A tower dump refers to the data related to a specific Base Transceiver Station’s activity. It will contain a log of all the activity carried out using the tower (calls, text, …) but also the list of all devices connected to the tower at a certain point in time, including passive connections (as we mentioned before, a device is always connected to a tower even if it is not actively doing anything.)
PCMD, RTT, NELOS#
Until now, we only saw things that would allow pinning a device to a pretty wide location. In this part, we will mention systems that may allow pinpointing a more accurate (but still pretty approximate) location. An AT&T document assesses that its accuracy is likely better “better than 100m”, and “better than 10km” depending on the cases.
PCMD (Per Call Measurement Data) and NELOS (Network Event Location Systems - AT&T Proprietary) are different names for mechanisms doing the same thing: since we know how fast radio waves travel, towers will measure the time it takes for data to travel between the tower and connected devices, and compute an estimate of the receiver’s distance.
PCMD data is typically stored for a shorter time than data like CDRs (typically about one or two weeks). Some operators will not have this data (PCMD is only usable with CDMA networks, but things like Timing Advance are more or less equivalent), some will keep it for a week, and others for up to three months.
PCMD data will normally just be recorded when data transfers are occurring (Internet/Call/SMS) but some operators might have different policies depending on the type of data.
Real-Time Location#
The methods we discussed until now are mostly based on activity logs, but there are also means to track a phone in real-time. The most common is triangulation (but some operators like Sprint also offer things like GPS pings to send a request to the phone to return its current GPS position).
Triangulation using Time of Arrival (TA) and Round Trip Time (RTT) measurements is a method widely supported by phone operators. It consists in having multiple towers pinging an endpoint and then measuring its distance with TA or RTT (based on the time it took for the radio waves to reach the devices).
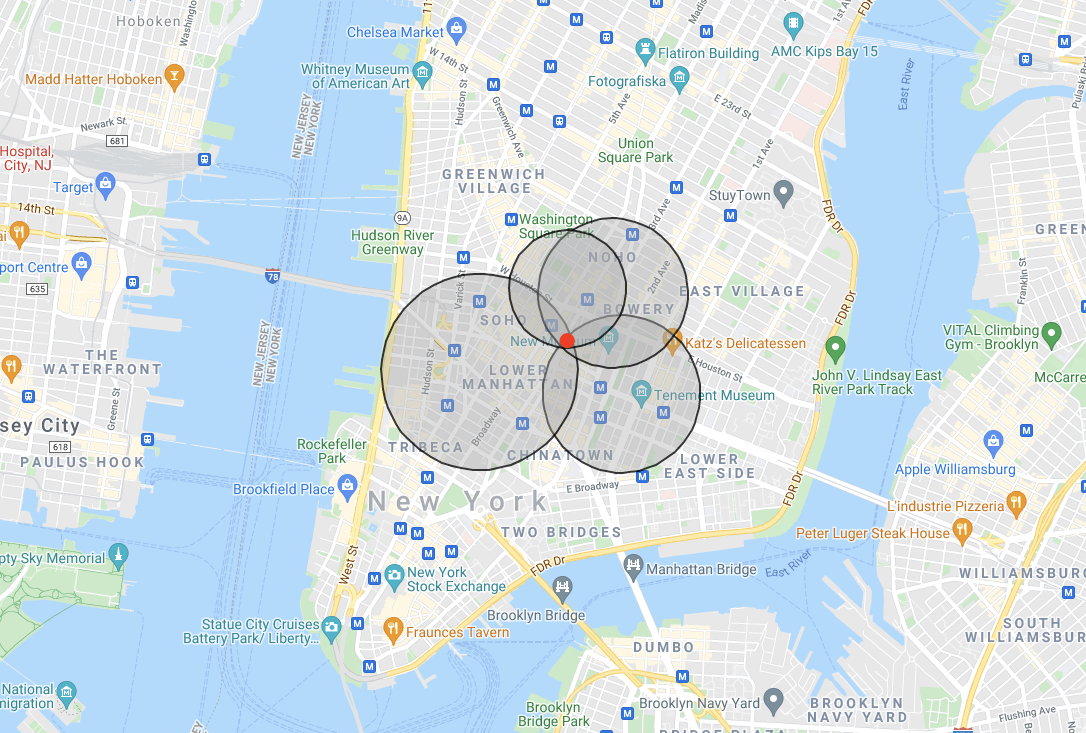
The figure below is an example of triangulation done by 4 towers. Each circle symbolizes the calculated distance from a tower, and we can see that all the distances have a single (red) point in common, which is the endpoint that we wanted to locate. Of course, the more towers there are, the more the location will be accurate, but the radius will likely be 50-100m at best.
Conclusion#
We discussed in this article how the phone network works, how it keeps logs (and what information they contain), and how it is possible to find a phone position in real-time. Based on this, we can conclude that as long as you are carrying a powered-on phone in a place with connectivity, you will leave some tracks. The only solution about that is to not have a phone, or to keep it off when possible (therefore reducing its usefulness a lot.)
If you are interested in the topic, you can check the various sources linked at the end of this article, but also things like IMSI-catchers (phone eavesdropping devices).
Sources and Extra-Resources#
- Comparison of mobile phone standards (Wikipedia)
- Cellular network (Wikipedia)
- How to Find a Cell Phone Tower Near You (Web Boost)
- Difference between GSM and GPRS (Geeks for Geeks)
- Introducing radio spectrum (GSMA)
- Difference between TDMA and CDMA (Geeks for Geeks)
- March 2019 FBI CAST Cellular Analysis & Geo-Location Field Resource Guide (FBI)
- Mobile Networks - Handover (YouTube - Mario Neugabauer)
- Base Station Controller (BSC) (Techopedia)
- Mobile Switching Centre (Olivia Wireless)
- Mobile Switching Center (MSC) (Techopedia)
- What Is a Mobile Switching Center (MSC)? (Emnify)
- Home Location Register (HLR) (Olivia Wireless)
- Visitor Location Register (VLR) (Techopedia)
- Cellular Analysis for Legal Professionals (Guardian Digital Forensics)
- CRIMINAL DEFENSE - LOCATION DATA Advanced Cell Site Analysis Using Per Call Measurement Data (IRIS LLC)
- Scientific Working Group on Digital Evidence (SWGDE)
- Cell Phone Investigations™ (Aaron Edens Police Technical)
- Cellular Records Review and Analysis Part 1: AT&T
- CELLULAR SERVICE PROVIDER (IRIS LLC)
- CELL-PHONE TECHNOLOGY (Wikieducator)
- Cellular Provider Record Retention Periods (Forensic Focus)
- Gotta Catch ‘Em All: Understanding How IMSI-Catchers Exploit Cell Networks (EFF)
Image Credits#
- Cover Photo by Kabiur Rahman Riyad on Unsplash