For obvious reasons, if you are doing shady business on darknet-markets, you don’t want to leave any tracks leading to you. Therefore, you would avoid using an email to register there, and that’s probably why most of the platforms do not ask for it; right? That being said, almost all of the dark markets are making use of PGP for various means such as secure communication, 2FA, … As PGP can be pretty obscure for some people, and as software are generally asking for an email address while generating PGP keys, it can allow us to gather some potentially interesting data depending on what users choose to input.
Point Market is very kind to offer an API that allows accessing pretty much everything within the market. From there, we can obtain data on 296 different stores (one store is a vendor). We can notice that 295 vendors have a PGP key set for their account.
After ingesting the data, we can observe that the vast majority of emails seems to be valid (and the majority of them is hosted at Gmail!). There are however a couple of smart vendors who did not input any email (or an obviously fake one) while generating their PGP key.
However, getting the emails alone may not be very speaking by itself as, while some provider vendors chose are definitely not a good choice, in an OpSec perspective, accessing the emails with a correctly configured Tor environment might not be that dangerous. To assess which emails might be used outside of the market, we added two metrics to the following graph. The red line is the number of vendors that do not have their name in the email associated with the PGP key, and the yellow line is the number of unique addresses having at least been pwned one time (source: haveibeenpwned.com). The blue line is just the number of PGP key associated with an email in the mentioned domain.
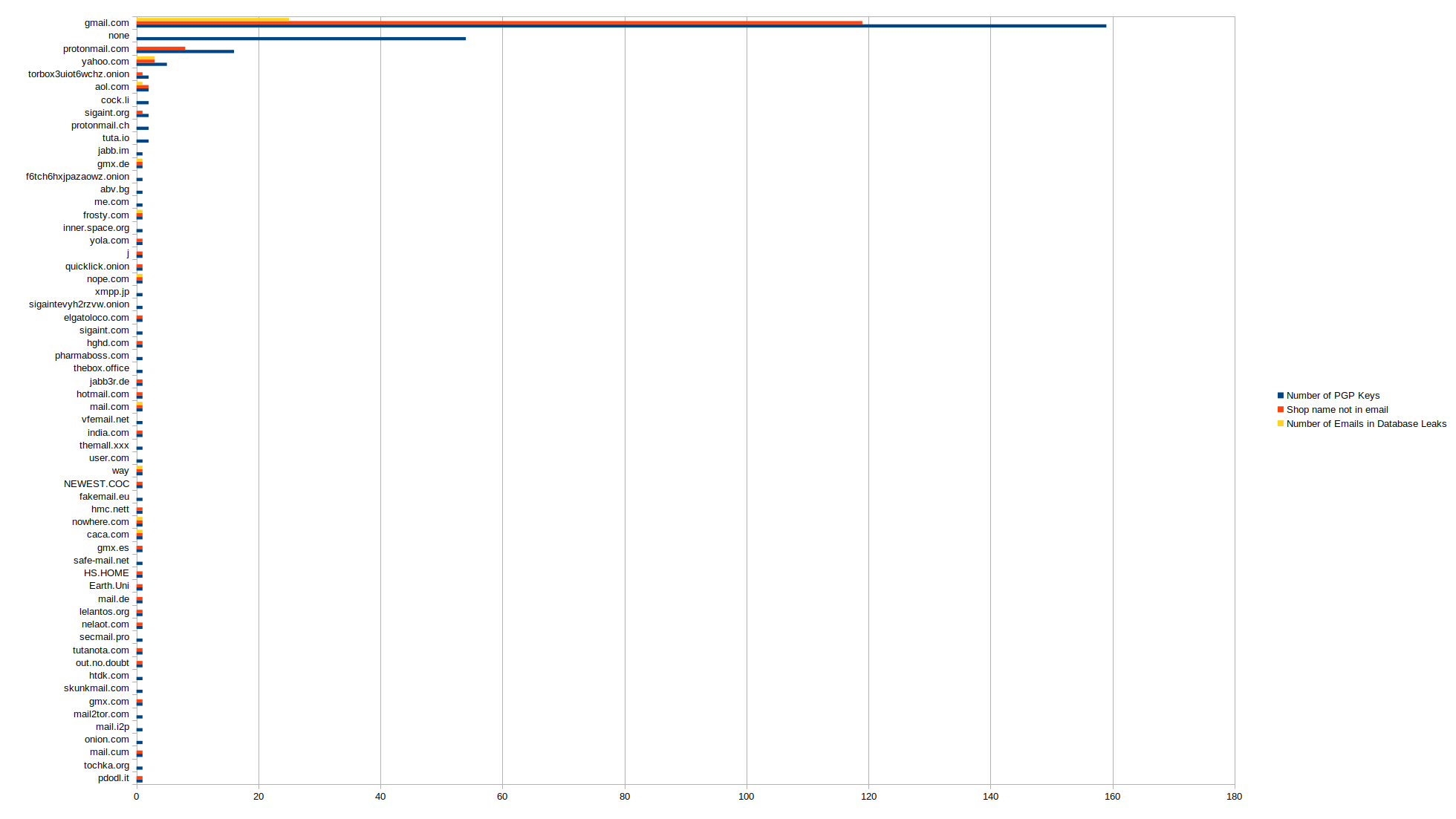
While the red metric offers a discussable representation of the reality, the number of pwned accounts can be a useful metric as it allows us to see which accounts are used and where. Moreover, surprisingly, it seems that plenty of accounts have been breached, which suggests that some vendors use the emails on common services, raising their chances to leave tracks leading to them. Let’s assess how bad that is by looking at what kind of services are compromised.
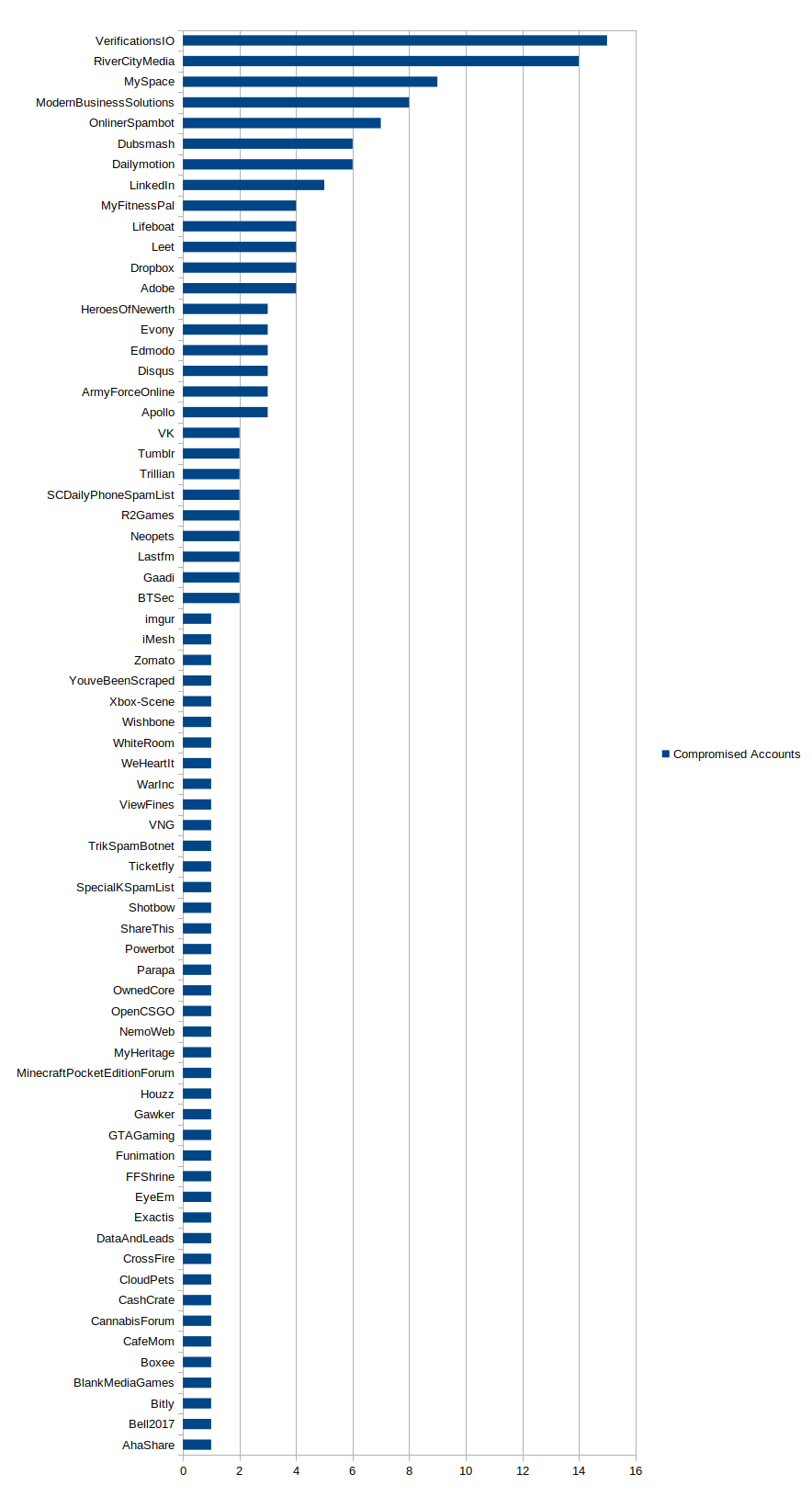
What we can first observe is a large number of services (69 for 25 unique users) where the various emails have been used. Note that to compute the graph, obvious fake emails domains have not been included as well as two Gmail addresses that seem to be potentially false (jb@yahoo.fr and SP@gmail.com).
Some services make sense when we consider the kind of business people are conducting (e.g. Cannabis Forum or Online Spambot), even if it still doesn’t seem like a good idea not to use a single email per service. However, some sound like a terrible idea such as Adobe, MyFitnessPal, TheTVDB, Edmodo or Funimation. Even if used with secure Tor settings, Adobe could launch an unexpected update, MyFitnessPal can give away what kind of products/band the user is eating, TheTVDB and Funimation what kind of movies/shows he likes, and Edmodo is a running app, it is supposed to be used with a GPS! All this information combined can give pretty useful personal identifiable information to be able to track a user.
Of course, it is possible that some of the emails in the breach are still fake (for instance used in the PGP but not belonging to a specific user), but it would make little sense to use a random-not-obviously-fake email. At the same time, some addresses not breached are used elsewhere (example on Twitter with an attributed phone number). A more in-depth analysis of these addresses, as well as some attempts to use various OSINT sources, will be done in future articles.