If you are using a VPN, maybe you are thinking “Well, my ISP has no idea of what I’m doing, and nobody can track me.” This might however not be completely true due to a common VPN issue: the DNS leaks. In this article, we will see what they are, what are their consequences, how to detect them, and some of the most common causes of leaks.
What are DNS leaks and their consequences?#
The following figure shows what happens when your VPN works as expected vs when there is a DNS leak. In the first case, you can see that the DNS server is reached through the VPN. Because of that, it is not possible for your ISP to see your DNS requests (which are unencrypted.) Unless you are using the DNS server provided by your VPN provider, the owner of the said server will not be able to know that you are the one trying to resolve a mysite.com.
In the case where you have a DNS leak, your computer will connect to the DNS server without using the VPN, which means that both your ISP and the owner of the DNS server (by default the ISP) will be able to see the sites that you are trying to resolve.
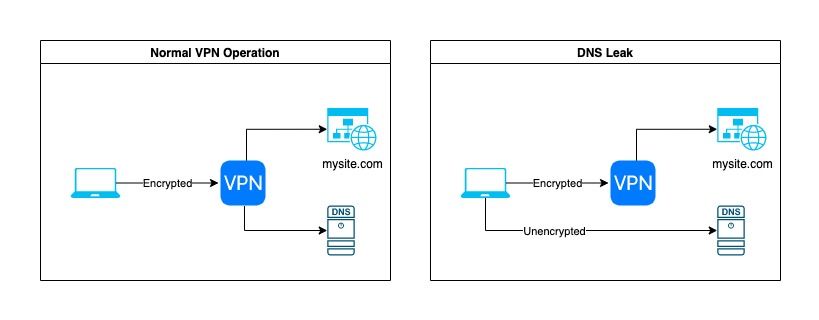
Depending on the reason why you are using a VPN, DNS leaks can be more or less bad. If you are in a country governed by an authoritarian regime and trying to access censored websites, then the authorities might be able to see that you accessed these websites and cause you some trouble. If you are just using VPNs to download your favorite Linux distribution by torrent, then it will be relatively harmless.
How to test for DNS leaks#
Third-party services, and how they work#
Testing for DNS leaks is pretty simple. You can use websites such as dnsleaktest.com or ipleak.net. Each of them will display your current IP address and the DNS server that you are using. My recommendation is to use your VPN provider’s DNS. The reason is that he already sees all of your traffic, so there is no point in adding another intermediary for domain name resolution. If you follow this recommendation, you should see your VPN provider’s DNS listed, and nothing else.
The way ipleak.net and similar websites work to determine what DNS servers you are using is pretty simple. When you load the page, they will give you a unique user ID. For example, abcd123. From there, they will make multiple requests to an API located at a subdomain containing your unique user ID. For example:
https://abcdefg123-1.ipleak.net/dnsdetectionhttps://abcdefg123-2.ipleak.net/dnsdetectionhttps://abcdefg123-3.ipleak.net/dnsdetection
This API will return the IP address of the DNS server that made the query. The reason why they do multiple calls is to be able to detect all of your DNS servers if you have more than one.
This doesn’t answer the question of how Ipleak knows your DNS server address. The way they manage this is the following: since the subdomain (e.g. abcdefg123-1.ipleak.net) you are trying to reach the API at is pretty unique, there is no chance that it is stored in your DNS cache or that anyone will try to resolve it at the same time. That means that you will need to ask Ipleak’s authoritative DNS server to resolve the subdomain for you. Doing so, your DNS server will contact Ipleak’s DNS server which will log the IP doing the request and store it to be accessible by the API.
Packets inspection#
Using online services to test DNS leaks is convenient, but sometimes it could be that the results are unclear. For example, if you use a non-standard DNS server, how can we be sure that you connect to the said server through your VPN and not directly?
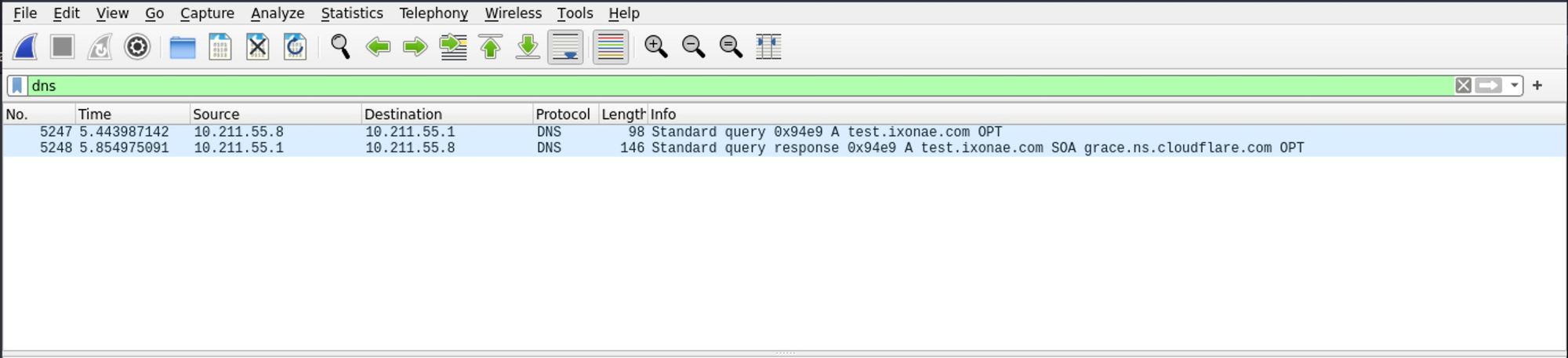
In that case, you can use Wireshark to see the packets actually leaving your computer. You just have to select your WiFi and/or Ethernet interfaces, and capture the packets going through. In the display filter, enter dns so that only the relevant queries show up. Then, try making requests to random domains. If nothing shows up in the captured packets, congratulations, it means that the DNS queries are routed through your VPN adapter are are not leaking. Otherwise, you need to inspect your configuration.
What causes DNS leaks#
While using the standard VPN configuration provided by a reputable provider should prevent DNS leaks, there are multiple things that can cause them. Some of the most common are:
- Transparent proxies
- Split DNS tunnels
- Unusual network routing configuration
- Windows’ Smart Multi-Homed Name Resolution
One concrete example of that would be if you are using your own DNS resolver with pfSense (see my previous article.) In that case, forgetting to set the Outgoing Network Interfaces to your VPN one will cause DNS leaks.
Conclusion#
- DNS leaks can enable your ISP and the owner of the DNS server that you are using to track your web activity by knowing which domain names you tried to resolve
- If you use a reputable VPN provider and its default configuration including its DNS servers without doing specific network configuration, you are probably safe
- You can (and should regularily) easily check if your configuration is DNS leaking
Sources and Credits#
- Cover photo by Daan Mooij on Unsplash